Introduction
8Base ransomware are an English and Russian-speaking threat actor group based in Russia. The group emerged in 2022 but rose to in prominence in May 2023. 8Base operates as a ransomware-as-a-service (RaaS), providing tools and infrastructure to affiliates who infect organisations’ networks in exchange for a cut of the payment. The 8Base ransomware binary is based on the ransomware variant Phobos due to the similarity in code and 8Base have been known to exploit vulnerable VPN appliances without Multi-factor Authentication (MFA).
Tools Used
The analysis used the following tools:
- Windows 11
- IDA Free
- X32dbg
- PEStudio 9.30
- CFF Explorer VIII
- Detect It Easy v3.09
- Strings.exe (Sysinternals)
Static Analysis
Malware Details
| Name | Fast.exe (8base ransomware binary) |
| Size | 68096 bytes |
| Type | PE32 executable for MS Windows |
| MD5 | 87D6D2488B1260E70F4042BF1F292529 |
| SHA1 | 161F9A79F8197C9B5DE1BEB7BD4D425D5C23B45B |
| SHA256 | 45DE59851D68929632346D6F894DC8C1B6A5C4197DB83C2E33C60631EFC0B39F |
| ssdeep | 1536:/NeRBl5PT/rx1mzwRMSTdLpJy/jIlkugRGVy/SR1qo+tEgfNni:/QRrmzwR5JysFV12i |
| Entropy | 7.303 |
| Compile Time | 31/03/2020 14:17:25 UTC |
| Signed? | No |
| Packer Info | N/A |
Sections
| Name | Virtual Address | Virtual Size | Raw Size | Entropy | MD5 |
| .text | 0x00401000 | 0x00008598 | 0x00008600 | 6.588 | A491C4D91A4B5889442E891DA7AAD09F |
| .rdata | 0x0040A000 | 0x00000E7C | 0x00001000 | 5.278 | A73FADB324BBEEC4E8315214D839BD02 |
| .data | 0x0040B000 | 0x000026B9 | 0x00000600 | 6.216 | CE2FE50C2F13EB409131F3EE88EF086B |
| .cdata | 0x0040F000 | 0x000062B8 | 0x00006400 | 5.696 | F919AED86A9B6CD7CB79BFA453DC462E |
| .reloc | 0x0040E000 | 0x000005EE | 0x00000600 | 7.921 | 63531957A01468434C794B6B08C13046 |
File Properties
This executable is a 32-bit executable for the Windows Operating System. The first two bytes of the header are MZ which confirms that this file is an executable file. The ransomware binaries developers wrote the program in C\C++, compiled using Microsoft Visual, and linked using Microsoft Linker. An interesting item to note is that the compilation timestamp is 31 March 2020 which is 2 years before 8base formed.
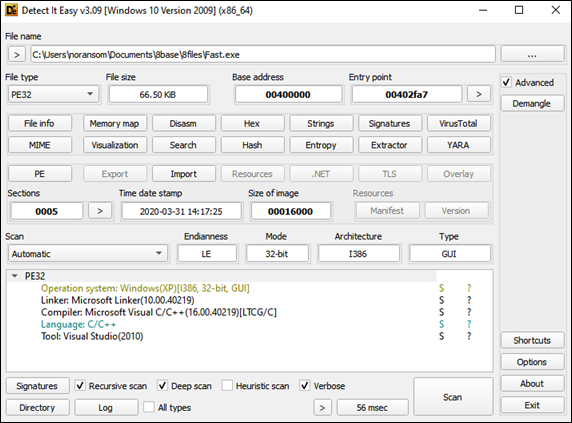
Strings and Imported/Exported Functions
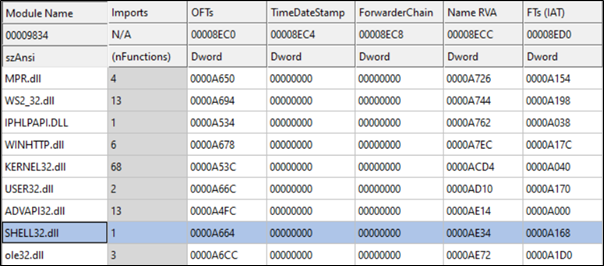
The ransomware binary contained strings and referenced imported functions and libraries. While execution may reveal additional strings, these are the ones present when using the programs Strings and PeStudio. A full list of Strings are in Appendix A.
8Base utilised the following Microsoft Windows system libraries.
Code Analysis
Drive Enumeration
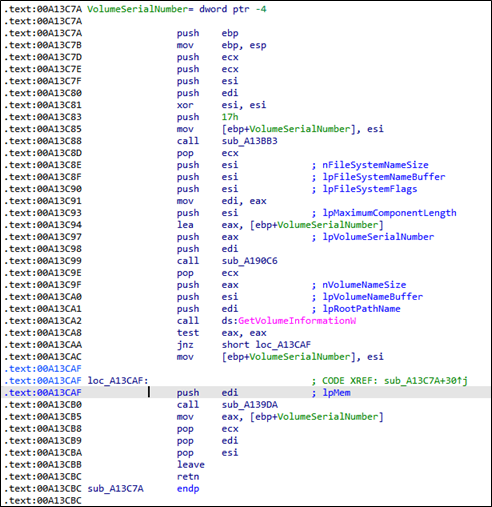
The 8Base ransomware binary starts by querying the available drives on the system using the Win32 API function GetLogicalDrives. By knowing which volumes are on a system, this allows the ransomware binary to encrypt data on, not only the C drive, but also other drives on the system.
Process Termination
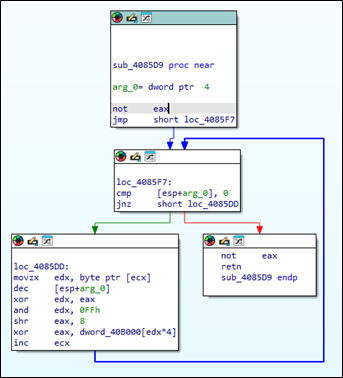
After executing, the ransomware binary, it terminates a specific set of programs before continuing to maximise damage against an organisation. The function CreateToolhelp32Snapshot enumerate all running processes and then terminates them using TerminateProcess. The figure below illustrates this behaviour.
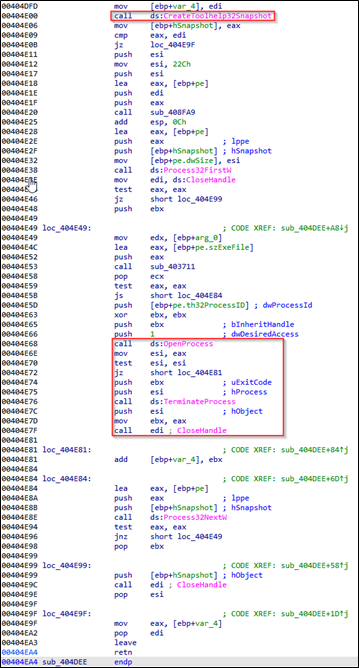
The figure and table below shows programs terminated by the ransomware binary. X32dbg retrieved this information and presented it in an easy-to-understand way.
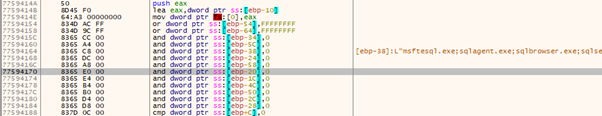
| msftesql.exe | sqlagent.exe | sqlbrowser.exe | sqlservr.exe | sqlwriter.exe |
| ocssd.exe | dbsnmp.exe | synctime.exe | agntsvc.exe | mydesktopqos.exe |
| xfssvccon.exe | mydesktopservice.exe | ocautoupds.exe | agntsvc.exe | agntsvc.exe |
| encsvc.exe | firefoxconfig.exe | tbirdconfig.exe | ocomm.exe | mysqld.exe |
| mysqld-opt.exe | dbeng50.exe | sqbcoreservice.exe | excel.exe | infopath.exe |
| mspub.exe | onenote.exe | outlook.exe | powerpnt.exe | steam.exe |
| thebat64.exe | Thunderbird.exe | oracle.exe | isqlplussvc.exe | agntsvc.exe |
| thebat.exe | mysqld-nt.exe | msaccess.exe |
Encryption Method
This binary contains no cryptographic libraries imported from the Windows API which means the ransomware binary itself implements any cryptographic functions. The developers likely did this because some environments limit programs’ access to the Windows crypto API. The ransomware binary encrypts all data on the system, with the exception of C:\Windows, using 256-bit Advanced Encryption Standard (AES256) in Cipher Block Chaining (CBC) mode and RSA.
When the ransomware binary comes across a file, it creates a copy, encrypts it, and then deletes the original file from the system. The ransomware binary deleting the original copy is to prevent organisations from recovering the files through volume shadow copies.
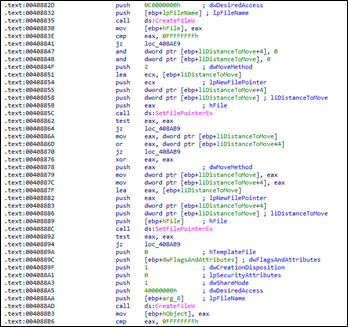
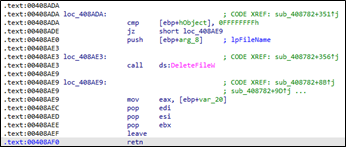
The ransomware binary analyzes the file size to determine if it exceeds 1,572,864 bytes. If the file is smaller than this threshold, the ransomware binary encrypts it entirely. Otherwise, the ransomware binary partially encrypts the file. It is worth mentioning that each ransomware group handles encryption differently.
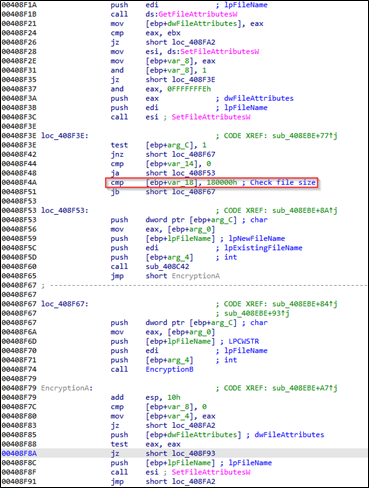
During the encryption process, the ransomware binary injects 0x40000 null byte blocks into the encrypted file.
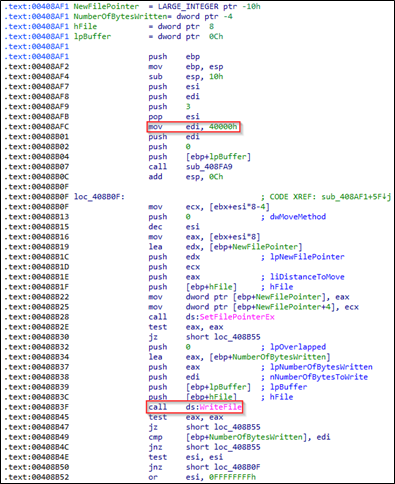
Here the ransomware binary generates the Initialization Vector values randomly. It encrypts the AES key using RSA.
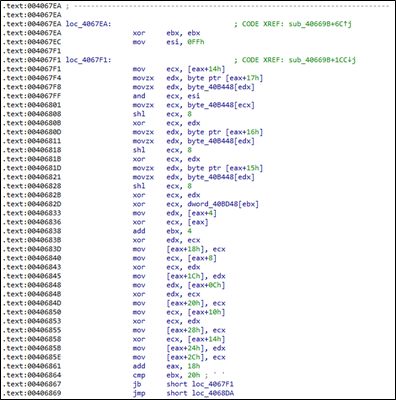
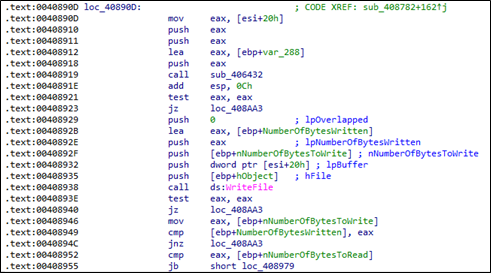
As the ransomware binary overwrites part of the file with null bytes, the program must store metadata related to the original values. The metadata is stored at the end of the file, where it encrypts the last 0xC0000 bytes, containing encryption details required for decryption if a decryption key is obtained.
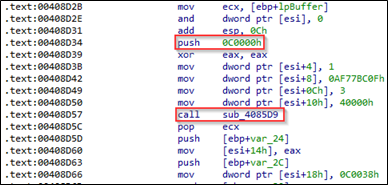
The files that become encrypted have the file extension “id[UniqueID].[recovery8files@onionmail.org].8base” appended.
Behavioural Analysis
The ransomware binary was detonated on an air gapped Windows 10 system with Microsoft Word and Steam opened. The encryption process took approximately 10 minutes to encrypt a Windows 10 system.
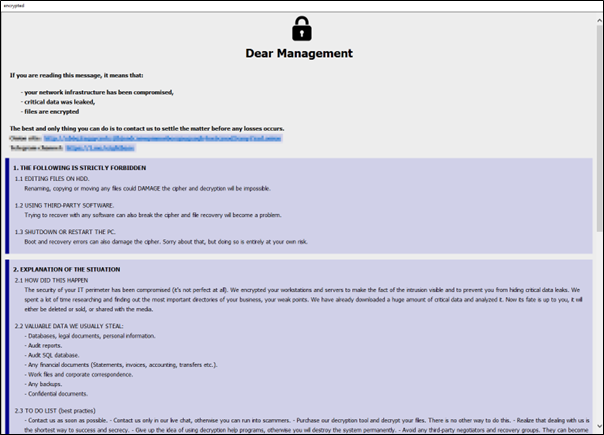
The ransomware binary terminated both Word and Steam, the encryption process begins as described earlier. During the encryption process, affected files were appended with the extension “id[UniqueID].[recovery8files@onionmail.org].8base”. The ransomware binary creates two files called info.hta and info.txt. The ransomware binary generates these files in the following locations.:
- C:\, and;
- C:\Users\<User>\Desktop
This file contains the ransom note and explains to the victim organisation how to decrypt their data and how to contact 8base.

Persistence
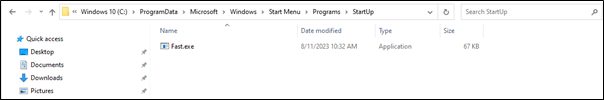
The 8base ransomware binary remains persistent within a client environment through the use of Startup Items and Autoruns. The StartUp items created were:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Fast: “C:\Users\%USERPROFILE%\AppData\Local\Fast.exe”
- HKCU\<User SID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Fast: “C:\Users\%USERPROFILE%\AppData\Local\Fast.exe”
- C:\programdata\microsoft\windows\start menu\programs\startup\Fast.exe
- C:\Users\%USERPROFILE%\AppData\Local\Fast.exe
- %USERPROFILE%\appdata\roaming\microsoft\windows\start menu\programs\startup\Fast.exe
- %ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup
One example of the ransomware binary dropping into a StartUp directory is shown below.
Defence Evasion
Volume Shadow Copy Removal
As part of the ransomware binary, it performs several actions to prevent system administrators from using Volume Shadow Copies and backup catalogs to assist in the recovery process. Additionally, the ransomware binary will ignore all boot failures when starting. The commands executed were:
- Vssadmin.exe delete shadows /all /quiet
- Wmic shadowcopy delete
- Wbadmin.exe delete catalog -quiet
- Bcdedit /set {default} bootstatuspolicy ignoreallfailures
- Bcdedit.exe /set {default} recoveryenabled no
Host-Based Firewall
The ransomware binary disables the host-based firewall on the system to allow inbound and outbound traffic.
- Netsh advfirewall set currentprofile state off
- Netsh firewall set opmode mode=disable
Recommendations
There are several recommendations which will assist in preventing the encryption of endpoints. However, it is important to note that this is not an exhaustive list.
- Implement an Endpoint Detection and Response (EDR) and SIEM tool.
- Audit accounts that require remote access on a frequent basis.
- Audit domain administrators and other high privileged accounts.
- Backup organisational data using the 3-2-1 method.
- You must have three (3) copies of your data,
- Two (2) stored on different types of media, and;
- One of those stored off-site.
- Update infrastructure as soon as possible in line with your patch management cycle.
- Use strong passwords and a password manager.
- Password length with a minimum of 15 characters.
- Use a combination of uppercase letters, lowercase letters, numbers, and special characters.
- Use passphrases.
- Use multifactor authentication for every account that supports it.
- Understand your attack surface. Look at different methods a Threat Actor could gain access to your network such as:
- Phishing
- Software vulnerabilities
- Exposed services
Appendix A: Referenced Functions
Strings found with PeStudio
- WNetEnumResourceW
- WNetUseConnectionW
- WNetOpenEnumW
- WNetCloseEnum
- WSAAddressToStringW
- GetIpAddrTable
- WinHttpReceiveResponse
- WinHttpOpenRequest
- WinHttpConnect
- WinHttpCloseHandle
- WinHttpOpen
- WinHttpSendRequest
- FindNextFileW
- OpenProcess
- FindFirstFileW
- MoveFileW
- GetCurrentThreadId
- SetFileAttributesW
- WriteFile
- CreateProcessW
- ReadProcessMemory
- TerminateProcess
- Process32FirstW
- Process32NextW
- CreateToolhelp32Snapshot
- DeleteFileW
- GetCurrentProcessId
- GetVolumeInformationW
- GetWindowThreadProcessId
- GetShellWindow
- FreeSid
- LookupPrivilegeValueW
- OpenProcessToken
- EqualSid
- RegSetValueExW
- AdjustTokenPrivileges
- LookupAccountSidW
- AllocateAndInitializeSid
- DuplicateTokenEx
- ShellExecuteExW